- Published on
- Updated on
Ransomware vs. Microsoft SQL Server
- Authors
Table of Contents
Many users encounter viral infections, and there are different types—some could slow down your computer and track your activities. Others block all operations, and these are the most dangerous.
Unfortunately, such epidemics have already become global. There is a significant number of security incidents that affect users; one of them is ransomware. How ransomware works is that it encrypts files—specific ones or all of them, detected on your computer—and extorts money from users. In some cases, users pay, but paying does not guarantee anything. It is unlikely that they can decrypt the documents. The epidemic started after the release of the WannaCry virus. Now it has a high number of followers. If your computer is already infected by ransomware, you have the following options:
- recover documents from backup,
- search your mailbox, and try to extract files from emails, or
- recover missing data from messengers.

But what do the largest developers do, Microsoft, for example? Do they have something to protect Windows from such incidents? Unfortunately, they cannot offer anything.
In the case where ransomware affects SQL Server databases, it is advised to use the latest backup for a DB restoration. Do not pay anything to virus developers. But what should you do, if the backup is encrypted as well?
Let us take a closer look at ransomware. Besides social engineering, viruses use existing software vulnerabilities to infect computers. Do not forget that infections also represent programs, sure they have their weaknesses, but which ones? That’s easy. Ransomware needs to encrypt the maximum amount of documents ASAP. Note any problem when it deals with relatively small files, such as Excel tables, Word documents, and others: in such cases it quickly encrypts tons of documents right after the infection. However, how to process huge files, i.e. databases? Note that in such cases the ransomware usually damages the document header without changing the DB itself.
In such cases, you may have excellent chances to recover databases affected by ransomware. Typically, Microsoft SQL Server keeps data in NDF and MDF files. If you take a closer look at these files, their size is enormous, many Gb’s, or even Tb’s. The system uses large HDD storages, like RAID arrays, to store this data. Each file has its header, having some service information, used for quick access, it contains references to data segments.
Ransomware usually damages the service data in question, but it is physically unable to encrypt all data pages within a reasonable time, so the ransomware developers typically leave it as is. Fortunately, it allows recovering affected databases without any efforts from you.
Since the developers of database applications cannot usually help, you need to look for third-party software to do this job. Owing to the absence of service information, we need an app to identify all data blocks inside a single DB file and try to recover the service information.
I would advise looking for a data recovery tool, supporting the restoration of corrupted Microsoft SQL Server databases. I think it is the same story. We need to access a file of MDF or NDF format that usually is not accessible. It means that the software we are looking for should be able to open corrupted (or partially encrypted) database files for analysis and recover data when it is possible. I would advise trying Recovery Toolbox for SQL Server (https://sql.recoverytoolbox.com/). This application is compatible with all available versions of Microsoft SQL Server, so you should not care about this matter, the same software installation allows opening any file of supported format.
How to Recover SQL Server DB After a Ransomware Infection
Recovery Toolbox for SQL Server (https://sql.recoverytoolbox.com/), as per its title, recovers corrupted databases of Microsoft SQL Server format, it does not have many parameters to configure. The software uses a step-by-step wizard, so users do several easy actions, as follows:
- choose a file of MDF format that is not openable typically,
- select a suitable recovery option and a target location for output data,
- choose data to be recovered and
- start the data recovery engine.
At the first step, Recovery Toolbox for SQL Server analyzes and parses a database of SQL Server format and note this process may take a great deal of time. The recovery time depends on many things: file size, data complexity, hardware performance, and the like. Just do not interrupt the analysis; you should wait until it is completed. Otherwise, you will find you need to start from the very beginning once again.
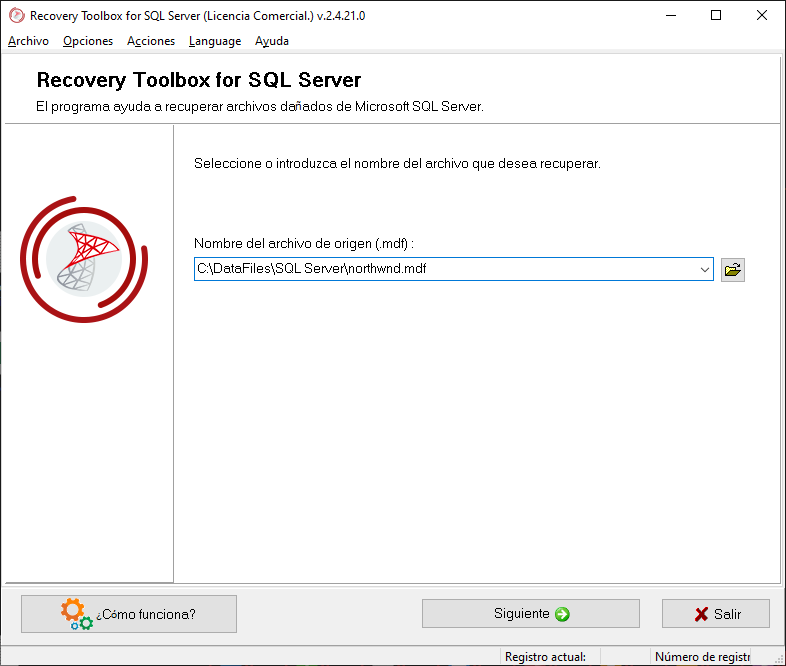
As soon as the analysis is completed, Recovery Toolbox for SQL Server displays data in the form of tables, and it is not exported anywhere at this stage. Users may evaluate the efficiency of analysis by browsing through data recovery sheets containing tables, procedures, functions, and other sections. In case the Recovery Toolbox for SQL Server successfully opens a database, encrypted by ransomware, there is no need to pay, just start the recovery routine. Note that demo version of Recovery Toolbox for SQL Server is free. The program allows evaluation of the results of the database analysis so you can decide to buy it if you find the recovery works fine for you.
In the very end, Recovery Toolbox for SQL Server allows choosing the output path to save data. This application can save it as SQL scripts into separate files or export the results to a new DB of Microsoft SQL Server format.
Note that we do not know how the ransomware encrypts data in your specific case, some parts of data could be lost, Primary and Foreign keys could also be affected. Feel free to analyze a corrupted database to check how it works.
Do the following to export recovered data to a new database of Microsoft SQL Server format—use the install.bat file, composed by Recovery Toolbox for SQL Server, the script should be located in the output folder, where other SQL scripts are located. Do not forget to provide the required database parameters, such as DB name, username/password, and server name. In some cases, the script should be executed more than a single time.
Note that all these actions are not needed if you have a good and recent backup. So, never forget about backups, it is the best way to keep your data safe.
Result: 0, total votes: 0

I'm Vladimir, your guide in the expansive world of technology journalism, with a special focus on GPS technologies and mapping. My journey in this field extends over twenty fruitful years, fueled by a profound passion for technology and an insatiable curiosity to explore its frontiers.